Cloud Computing With Security Concepts And Practices: Your Essential Guide to Secure Cloud Adoption

In the ever-evolving world of technology, cloud computing has emerged as a transformative force, revolutionizing the way businesses operate and leverage data. However, with the immense benefits of cloud computing come inherent security concerns that organizations must address to protect their sensitive information and maintain operational integrity.
5 out of 5
| Language | : | English |
| File size | : | 63469 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 518 pages |
This comprehensive guide, "Cloud Computing With Security Concepts And Practices," serves as an invaluable resource for professionals seeking to master the intricacies of cloud security. Written by industry experts, this book provides a comprehensive overview of cloud security architecture, data protection strategies, and risk management best practices, empowering readers to confidently navigate the complexities of cloud computing.
Chapter 1: Understanding Cloud Security Architecture
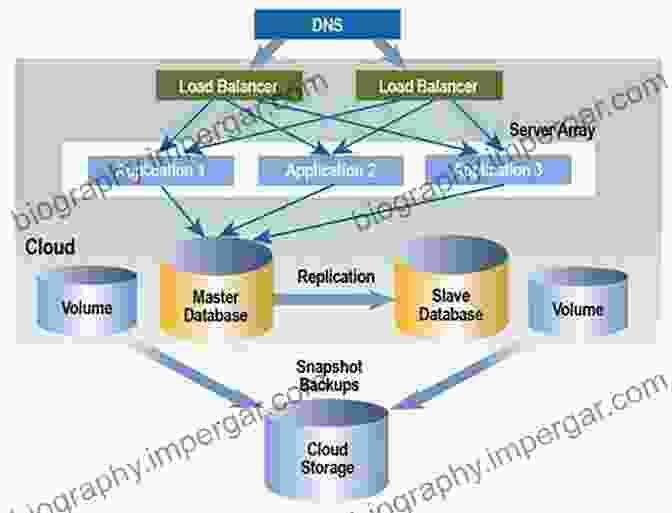
The book begins by establishing a solid foundation in cloud security architecture. It explores the various cloud deployment models (public, private, hybrid, and multi-cloud) and their associated security implications. Readers gain a clear understanding of cloud security boundaries and the shared responsibility model, enabling them to make informed decisions about cloud adoption.
Chapter 2: Data Protection in the Cloud
Data protection is paramount in cloud computing. Chapter 2 delves into the fundamentals of data encryption, both at rest and in transit. It also covers key management strategies, data access controls, and mechanisms for data loss prevention. By understanding these concepts, readers can effectively safeguard sensitive data in the cloud.
Chapter 3: Risk Management in Cloud Computing
Proactively managing risks is crucial for ensuring cloud security. Chapter 3 provides a thorough analysis of cloud security risks and vulnerabilities. It outlines risk assessment methodologies, risk mitigation strategies, and incident response plans. By following the guidance provided in this chapter, organizations can minimize the likelihood and impact of security breaches.
Chapter 4: Cloud Security Practices and Best Practices
Chapter 4 focuses on practical cloud security practices and best practices. It covers essential topics such as identity and access management, security monitoring, vulnerability management, and compliance with industry standards. By implementing these best practices, organizations can enhance their cloud security posture and reduce the risk of data breaches.
Chapter 5: Emerging Trends in Cloud Security
The cloud security landscape is constantly evolving. Chapter 5 explores emerging trends and innovations in cloud security, such as artificial intelligence (AI),machine learning (ML),and quantum computing. It provides insights into how these technologies can be leveraged to further enhance cloud security and stay ahead of potential threats.
, "Cloud Computing With Security Concepts And Practices" is the definitive guide for professionals seeking to master cloud security. Its comprehensive coverage of cloud security architecture, data protection strategies, risk management best practices, and emerging trends empowers readers to confidently embrace cloud computing while mitigating potential security risks.
Whether you're a cloud architect, security engineer, IT manager, or business decision-maker, this book provides the essential knowledge and practical guidance you need to harness the transformative power of cloud computing while safeguarding your organization's critical assets.
Free Download your copy today and unlock the full potential of cloud computing with security as your compass!
Free Download Now
5 out of 5
| Language | : | English |
| File size | : | 63469 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 518 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia 2nd Edition
2nd Edition Lillian Bradley
Lillian Bradley Thomas Worzyk
Thomas Worzyk Bhawani Singh
Bhawani Singh Mandy Hickson
Mandy Hickson Katherine Guzman
Katherine Guzman Jenny Doan
Jenny Doan Susan Neiman
Susan Neiman Raju L Bhardwaj
Raju L Bhardwaj Lisa Wedeen
Lisa Wedeen Richard Schickel
Richard Schickel 2000th Edition Kindle Edition
2000th Edition Kindle Edition Phillip Barlag
Phillip Barlag Arthur C Brooks
Arthur C Brooks Tee L Guidotti
Tee L Guidotti 2010th Edition Kindle Edition
2010th Edition Kindle Edition Clifford Thurlow
Clifford Thurlow Luce Giard
Luce Giard Mark Bratton
Mark Bratton Gunnar Stiesch
Gunnar Stiesch
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Timothy WardUnveiling the Power of Public Procurement Law: Hart Studies in Competition...
Timothy WardUnveiling the Power of Public Procurement Law: Hart Studies in Competition... Jeremy MitchellFollow ·18.5k
Jeremy MitchellFollow ·18.5k Chuck MitchellFollow ·11.3k
Chuck MitchellFollow ·11.3k Shaun NelsonFollow ·8.8k
Shaun NelsonFollow ·8.8k James JoyceFollow ·7.9k
James JoyceFollow ·7.9k Carlos FuentesFollow ·11.6k
Carlos FuentesFollow ·11.6k Roald DahlFollow ·11.2k
Roald DahlFollow ·11.2k Arthur C. ClarkeFollow ·16k
Arthur C. ClarkeFollow ·16k Jace MitchellFollow ·18.8k
Jace MitchellFollow ·18.8k

 Jeff Foster
Jeff FosterExploring Culture: Exercises, Stories, and Synthetic...
Culture is a complex and multifaceted...

 Eddie Bell
Eddie BellPrinciples of ICD-10 Coding Workbook: Your Comprehensive...
Empower Yourself with the...

 Nikolai Gogol
Nikolai GogolOttoman Egypt: A Catalyst for the Modern World's...
: A Hidden Gem in...

 Jorge Amado
Jorge AmadoUnveiling the Secrets of Group Intervention: A...
In the realm of...

 Dakota Powell
Dakota PowellUnveiling the Interwoven Nature of Animality and Colonial...
Welcome to an...
5 out of 5
| Language | : | English |
| File size | : | 63469 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 518 pages |